Cloud Computing
Posted On: , Author: Srikanth Jallapuram
At Technovature we have a solid expertise and an innovative approach in the niche of cloud computing, as we deliver a diverse range of cloud integration services, cloud computing solutions, and cloud computing services to help the business flourish and gain significant cost benefits in the current market domain.
We craft out the most innovative cloud software solutions that are scalable and allow the businesses to enjoy their perks. We design cloud solutions for addressing the distinctive infrastructure, database, computation, and storage requirements.
Enterprises use 1,427 distinct cloud services on average.
Cloud Advisory & Consulting
Cloud computing has achieved a high level of maturity with an ability to build a robust and elastic pay as you go IT infrastructure to support your Application Deployment needs in a matter of a few minutes once designed. However the real benefits are much more than that and Technovature can advise and consult with you to assess your existing IT Infrastructure and suggest the most efficient cloud architecture that can support a sustainable cost-effective cloud hosting and cloud deployment model supported by DevOps, API, Security and Automation that is the most suitable for your organization blueprint and your organization journey over a period of time.
Cloud Application Development
Building Cloud Native Applications is a highly loaded term. However we at Technovature understand that a diverse set of needs for your organization's digital transformation requires a robust cloud architecture that can help us build cloud native applications with a flexibility of different application frameworks, data science tool kits, serverless architecture, solid API management and interfaces powered by microservices, analytics, mobile and web backends, solid database applications and much more that can be achieved with an Innovative cloud development approach that Technovature can deliver with zest.
Cloud Integration and Software Solutions
Cloud integration is a system of tools and technologies that connects various applications, systems, repositories, and IT environments for the real-time exchange of data and processes. Once combined, the data and integrated cloud services can then be accessed by multiple devices over a network or via the internet. We help you break down data silos, improve connectivity and visibility, and ultimately optimize business processes. It is a response to the need to share data among cloud-based applications and to unify information components.

Sophisticated AWS solutions & implementation
Amazon Web Services offers a wide range of different business purpose global cloud-based products. The products include storage, databases, analytics, networking, mobile, development tools, enterprise applications, DevOps automation, with a pay-as-you-go pricing model. Important AWS Services. Here, are essential AWS services
Cloud Migration Services
At Technovature we can help you in identifying your business case for migration and help define your cloud roadmap, plan and execute your migration to the cloud, then work with you to take advantage of your new cloud-based solutions. Your business-critical applications and databases may need operational support, re-platforming or re-architecting. Complex scenarios such as working with difficult data and analytics use cases, with massive data volumes, many data pipelines, or complex environments, we can handle all of them for you.
Sophisticated AZURE Solutions Development
Technovature has an exclusive partnership with Microsoft Azure where we can help you design and build with an ever-expanding set of cloud services to help your organisation meet your business challenges. It is the freedom to build, manage and deploy applications on a massive, global network using your favorite tools and frameworks. Azure Cloud can help your organization be future-ready, build a cloud with high flexibility along with Microsoft's commitment to open source. We can help you operate your cloud on-premise, private, public or hybrid seamlessly with a solid security foundation from Microsoft that helps you build your own cloud that you can trust for your organization.
What is a Hybrid Cloud?
Hybrid cloud is a cloud computing environment that uses a mix of on-premises, private cloud and third-party, public cloud services with orchestration between the two platforms.
Cloud Statistics
The public cloud service market is expected to reach $623.3 billion by 2023 worldwide. While 83% of enterprise workloads will be in the cloud by 2020.
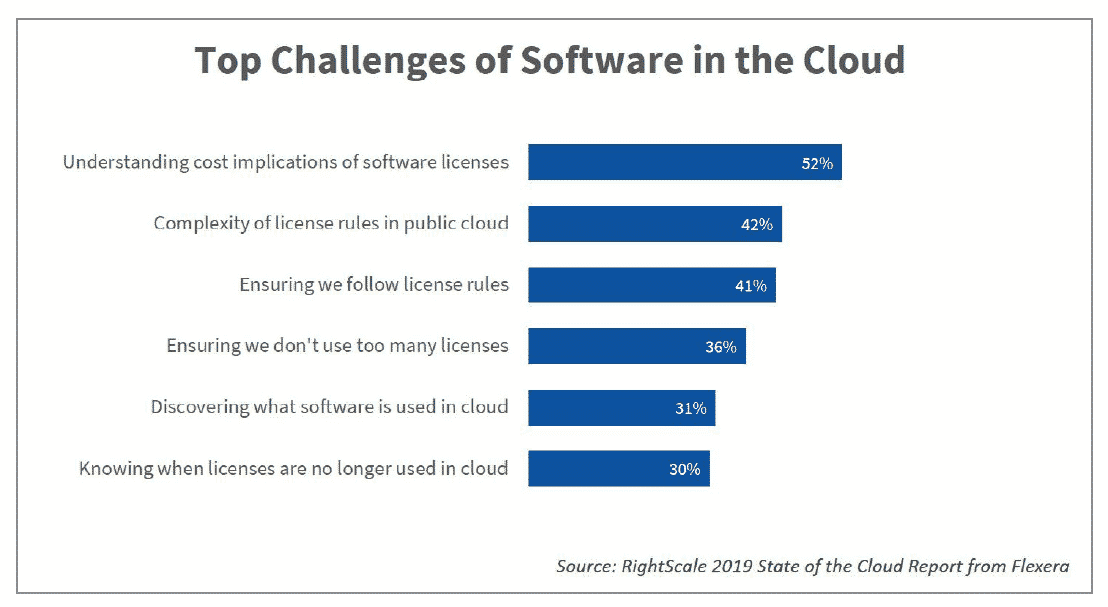
The #1 priority in 2020 is cloud cost optimization
So what are the Best Practices in Cloud Computing ?
There is a set of problematic issues that pose a significant threat to cloud users, such as:
- The degree of trust to the cloud service provider;
- Ensuring confidentiality, integrity, relevance, and incontrovertibility of information at all levels;
- Loss of data control and data leaks;
- Protection against unauthorized access;
- Malicious insiders;
- Saving personal data of users transmitted and processed in the cloud.
Security Breach
In November 2018, Marriott International announced that cyber thieves stole data on 500 million customers. The attackers’ targets were contact info, passport number, Starwood Preferred Guest numbers, travel information, credit card numbers and expiration dates of more than 100 million customers.
The cloud computing system can be exposed to several types of security threats, which can be divided into the following groups:
- Threats to the integrity;
- Threats to confidentiality;
- Accessibility risks;
- Authorization risks;
- Browser vulnerabilities.
Some key best practices in implementing cloud security in your organizaion are as below:
- Train Staff 💰 The users are the front line against threats to secure cloud computing. These users are staff and stakeholders of the company that utilizes the cloud computing network to access different functions through different touchpoints. These users should be well trained in spotting dangerous elements such as malware masquerading as legitimate applications or files.
- Look for trustworthy cloud security providers 💪 In a digital age of transparency and lightning-fast connections, privacy has become a serious concern. A breach in data such as a leak of customer personal information to hackers can result in costly lawsuits and compensations. Therefore, it is paramount that cloud cybersecurity providers are up to the task and understand the regulations surrounding cloud network security. These providers of security cloud services should provide documentation and reports on the process and status of the cloud network’s security.
- Look into the future 🙌 The internet is a rapidly growing place with new innovations being made. These innovations have led to the creation of more complicated and capable cloud cybersecurity threats. With the rapidly evolving risk, cloud computing security must look into the future and prepare for potential threats that the cloud network security might face. As such, cloud security should be regularly updated. This goes for both the software and the polices involved. The software needs to be able to fend off the threat while policy updates keep the process compliance with the latest industry standards.
- Encryption cloud-based security 💁♀️ For cloud computing to be secure, the data should be encrypted as it enters the cloud storage device. Moreover, in creating a secure cloud computing system, users should be able to send encrypted data to and from the network. It protects the confidentiality of data being transmitted. Also, it limits the level of access each user has within the cloud computing network.
- Deploying Cloud Security Management solutions 👫 A tactical cloud computing security best practice would be to implement identity and access management solutions to the cloud computing network. This process involves stopping threats from the user’s endpoint as its purpose is to screen the entities accessing the cloud computing network from a designated access point.
- Secure Endpoints 👫 Securing endpoints is a good practice for cloud computing security as it provides intrusion protection and access control. Endpoint security and cloud computing security used to be separated disciplines. However, changes in consumer behavior have led companies to adopt more open, affordable and accessible IT solutions for cloud computing. By integrating cloud computing security with the endpoints, companies are able to meet the round the clock demands of its customer base.
- Neutralize and removal of threats from cloud security 👫 One of the best cloud computing best practices is improving the speed of neutralization and removal of cyber threats. Cloud cybersecurity threats have become increasingly advanced. They are able to disguise themselves as innocently appearing resumes, invoices, and other common documents.
- Intrusion protection and prevention 👫 An intrusion protection and prevention system examines the files moving through the network to identify and prevent vulnerabilities that can be exploited. An intruder usually finds a way into the cloud computing network through input from an endpoint. The aim of such an intrusion is to interrupt the network and gain control of applications.
- Compliance Requirement 👫 Implementation of a cloud cybersecurity that meets the regulations of both the industry and governments has become a must as stakeholders are becoming increasingly connected in a rapidly globalized world. While compliance might seem intuitive, the process is made complex. This is because data and applications move from a controlled environment to endpoints in different countries, jurisdiction and regulations. The speed of communication and ease of use has given a sweet spot for chatbots in the Millennial audience compared to legacy tools.
- Conduct cloud security IT audits 👫 These cloud computing security audits are performed to determine if the network and its maintainers meet the legal expectations of customer data protection and the company’s standards for facing cloud cybersecurity threats. These audits should be transparent, cover the relevant scope and consider locational jurisdictions.